Testimony before the Subcommittees on Investigations and Oversight and Research and Technology, Committee on Science, Space and Technology, House of Representatives
Vijay A. D'Souza, Director, Information Technology and Cybersecurity, Government Accountability Office (GAO)
25 May 2021
Select excerpt from June 2021: SHIELDWatch Newsletter
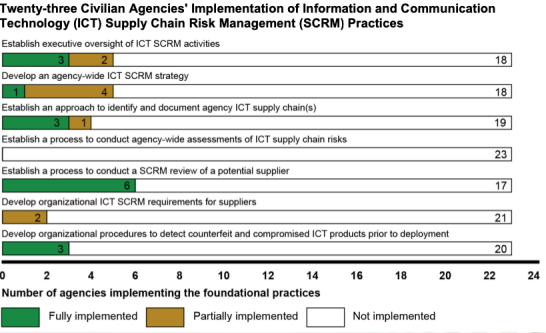
In testimony to the U.S. House of Representatives, the GAO Director for Information Technology and Cybersecurity identified a series of previous findings on vulnerabilities to the U.S. federal government’s Information & Communications Technology (ICT) supply chain, recommendations, and agency compliance status and impact for 23 federal agencies. Among the industries and technologies noted as having supply chains vulnerable to cyber-attack were pipelines, bulk energy, avionics, and 5G. Additionally, the GAO plans to release a detailed report evaluating federal agencies’ response to SolarWinds in fall 2021.